tl;dr
- Analysing ICMP type field and extracting GIF file
Descritpion
This is a good challenge and very useful challenge for learning about Networking and it’s related concepts.
Initial Analysis
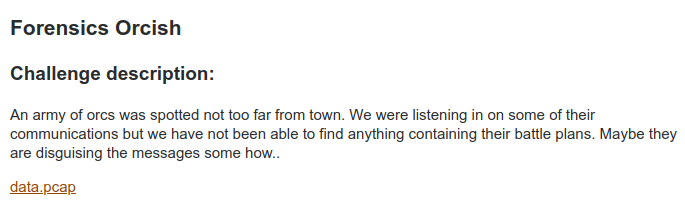
In this challenge on opening the pcap file and checking the protocol hierarchy, we can see so many protocols are present in it.
As usually, as there are so many HTTP and TCP packets in that, so using the Export objects we can extract the HTTP data from the packets. But could not find anything interesting from that. As we know that the same HTTP data is transferred via TCP also no need of extracting the TCP data from the TCP packets. I have wasted a lot of time in analysing those data and those packets.
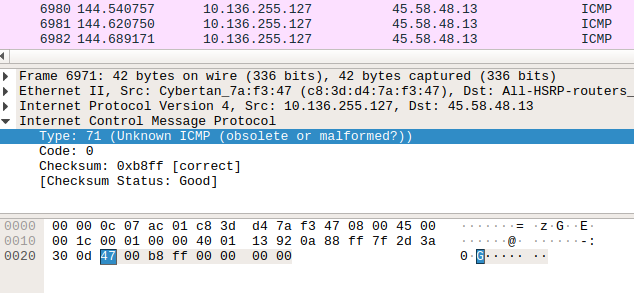
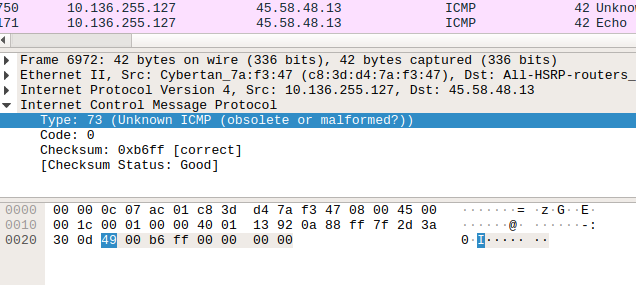
After going into ICMP packets, we can see the GIF file signature(GIF89a), splitted through upcoming packets. So we can assume that a GIF file is transferred in ICMP packets.
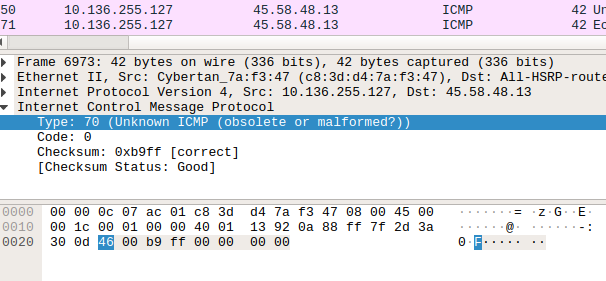
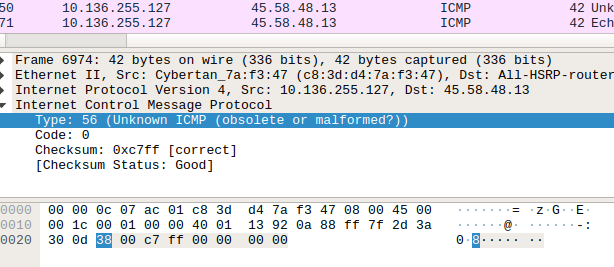
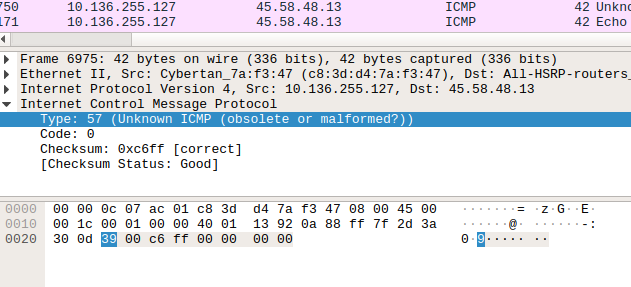
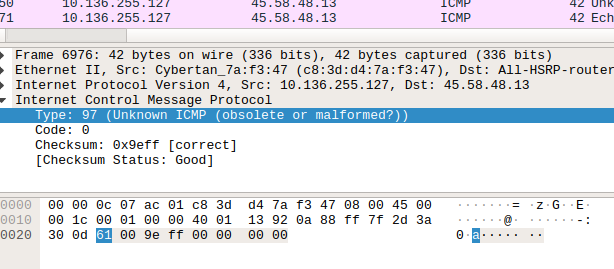
Further Analysis
So, we know that scapy a powerful packet manipulation program. Extracting the specified packets(ICMP) and reading the packet through scapy, we can see that, type layer of the ICMP packets was transferring the data.
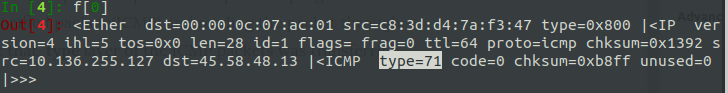
So, I have written an exploit script, to get the whole required data (ICMP type) from the ICMP packets. You need to export all the ICMP packets and save it as exported.pcap, and run the script below.
from scapy.all import *
f=rdpcap('exported.pcap')
x=''
for i in range(len(f)):
x+=chr(f[i][ICMP].type)
b=open('flag.gif','w')
b.write(x)
b.close()Flag
After running the above code it will create a new file named flag.gif and after opening it we got the flag.

If you liked my solution, please do share it. I’m available on Twitter: @NihithNihi

