tl;dr
- chrome history analysis
- File recovery from memory dump
- Simple stego
Description
Initial Analysis
We are given with a Windows 7 memory dump. Let’s see what all processes are running in the macine.
$ volatility -f for1.raw --profile=Win7SP1x86_23418 pslist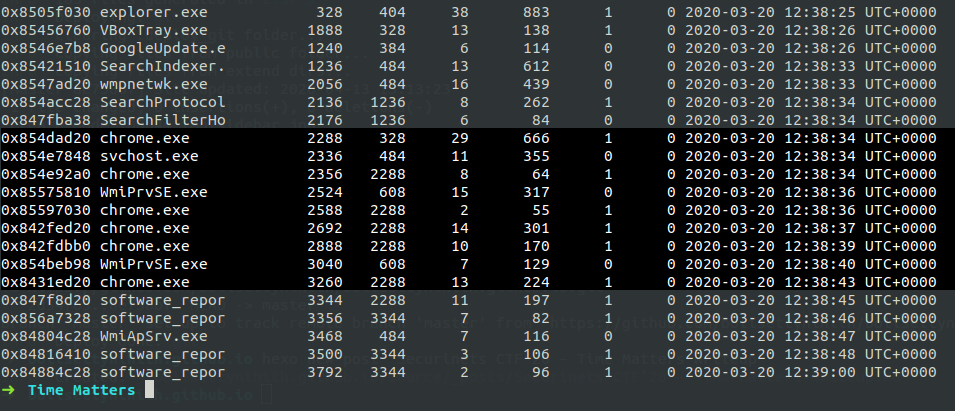
We can see Explorer and chrome are in open, lets check what’s there in Chrome’s history. We know that for their is a plugin chromehistory, we will use that.
volatility --plugins=/home/g4rud4/Downloads/Tools/volatility-plugins -f for1.raw --profile=Win7SP1x86_23418 chromehistory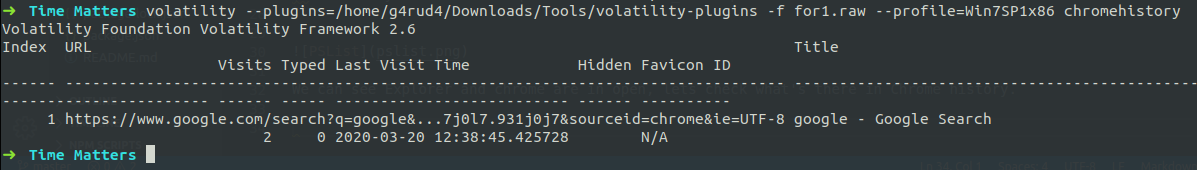
We didn’t find any suspicious links in chrome’s history.
Further Analysis
So let’s check what all files are there in the system.
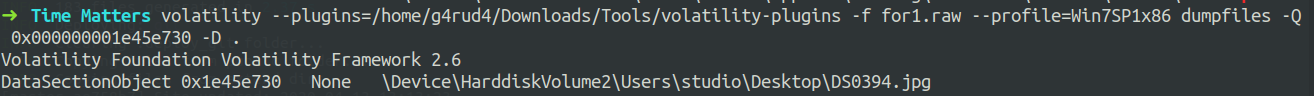
volatility --plugins=/home/g4rud4/Downloads/Tools/volatility-plugins -f for1.raw --profile=Win7SP1x86_23418 filescan | grep Desktop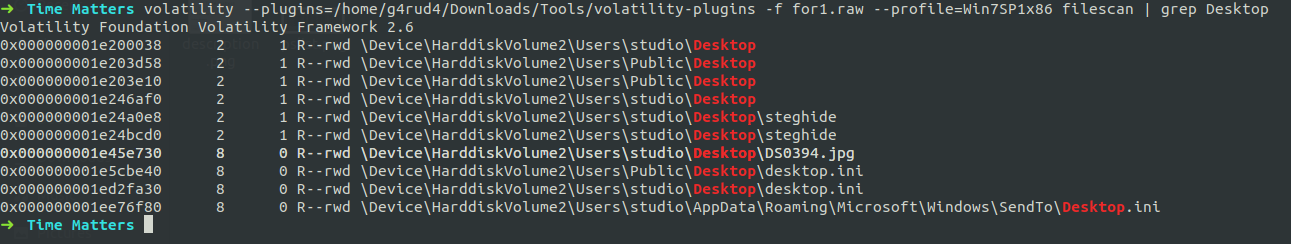
We can steghide and a jpg image on the desktop, So let’s dumpfile the jpg file and use steghide on it.
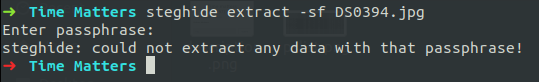
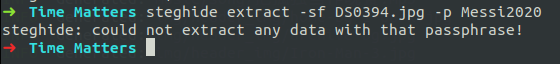
When I used steghide for extaction, it asked for the password, I followed the same way as everyone does, just leaving it blink and clicking Enter. But no use.
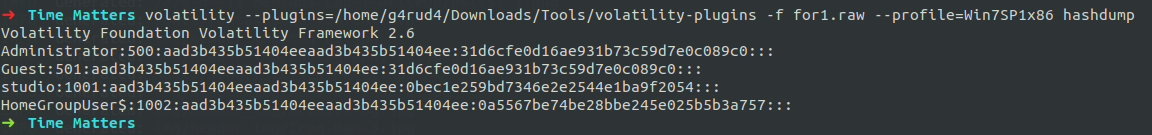
So I thought to use the users password and got the NTLM hash using hashdump, but when cracked hash didn’t gave the result.

Flag
So after opening the image, it’s Messi’s image which was took on 2019. So the on looking at the challenge titile and relating that to the password of steghide, we can use Messi2019 as password and try what we can get.

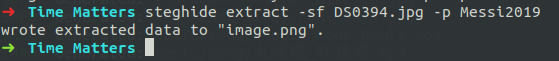
Hoorah!! We got the output. One opening the resulted image, we got the flag.

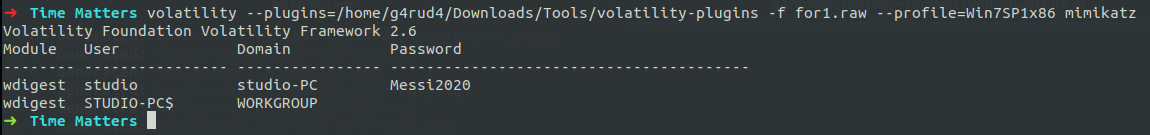
There is an other way also, by using mimikatz for getting the user password. But when I used the password that we got in mimikatz, I didn’t got anything, so after modifing the password by relating to the challenge title and modifying it to Messi2020, we can get the flag.
If you liked my solution, please do share it. I’m available on Twitter: @NihithNihi

