tl;dr
- Memory dump analysis using Volatility.
- Extracting Keepass Master Password from the memory.
- Extracting flag from ZIP archive attached in the Keepass database.
Description
I managed to forget my password for my KeePass Database but luckily I had it still open and managed to get a dump of the system’s memory. Can you please help me recover my password?
Challenge file: Mega Drive or Google Drive
Password: eD99mLkU
Hint: I am not very good with computers, I use my one safe password where I want to keep everything safe from hackers.
I solved this challenge after the CTF has ended.
According to the description, In this challenge, we have to retrieve the Master Password of a Keepass database from the memory.
Initial Anaysis
First, you need to find what OS his system was using. For that, I used imageinfo plugin.
$ volatility -f HackTM.vmem imageinfo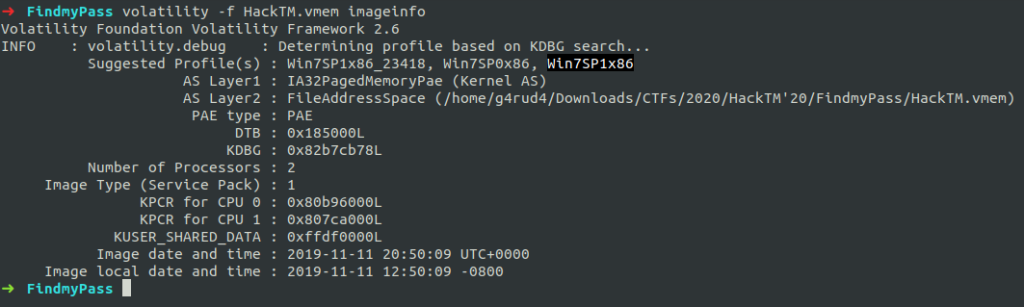
I choose Win7SP1x86 profile.
Let’s check what all processes are running in the system. We can expect that keepass.exe will be present, as the description says that the database was kept open.
$ volatility -f HackTM.vmem --profile=Win7SP1x86 pslist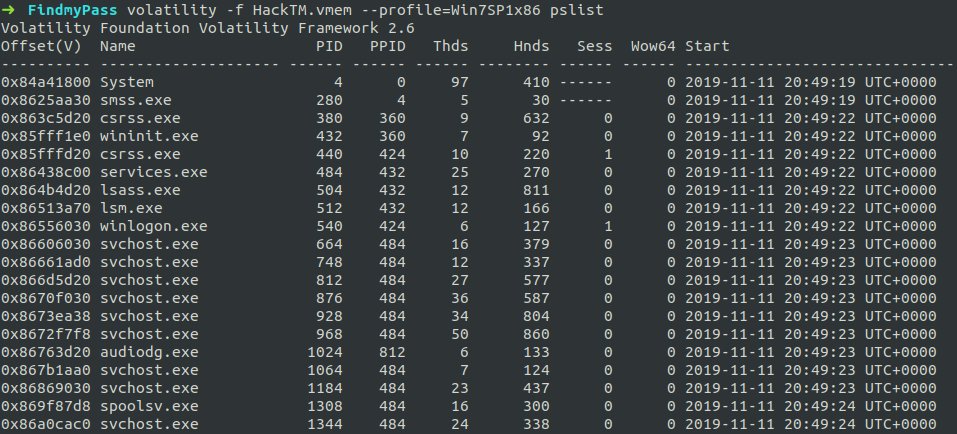
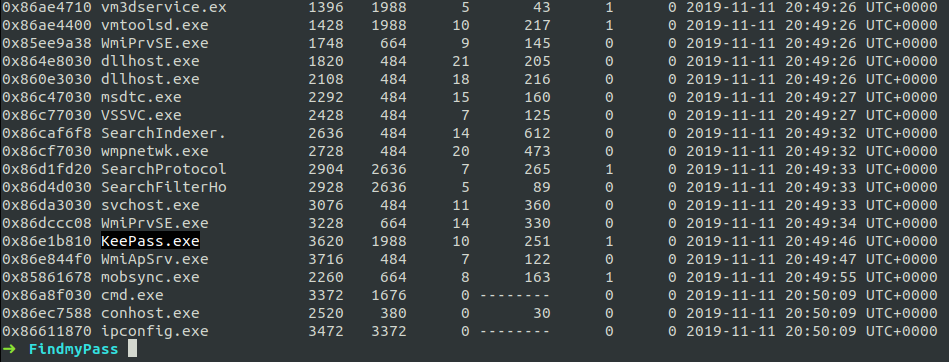
We can see that the keepass.exe process was running and going further.
Extracting Keepass database
We need to find the .kdbx file as all KeePass databases are stored with extension .kdbx. For that, we will use filescan plugin and grep for kdbx files.
$ volatility -f HackTM.vmem --profile=Win7SP1x86 filescan | grep ".kdbx"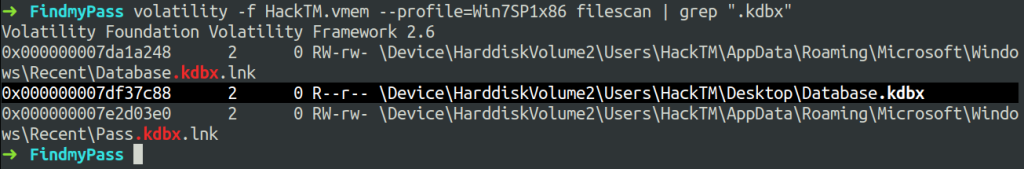
We can see a database.kdbx was open and the further step is to dump that file to our host system. For that, we will use dumpfiles plugin.
$ volatility -f HackTM.vmem --profile=Win7SP1x86 dumpfiles -Q 0x000000007df37c88 -D .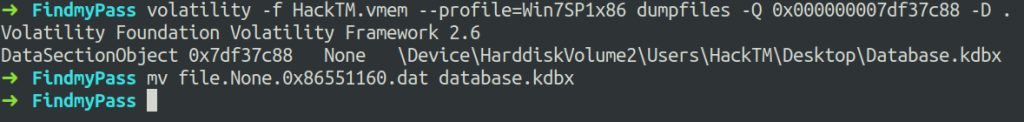
When I attempted to open the database, it asked for the master password. The description says that the user has forgotten his password which means we have to recover it.
Retriving Master Password
But the hint says user used the same password everywhere ie: he must have copied the password and user it somewhere else. So let’s check what’s there in his clipboard. For that, we use the clipboard plugin.
$ volatility -f HackTM.vmem --profile=Win7SP1x86 clipboard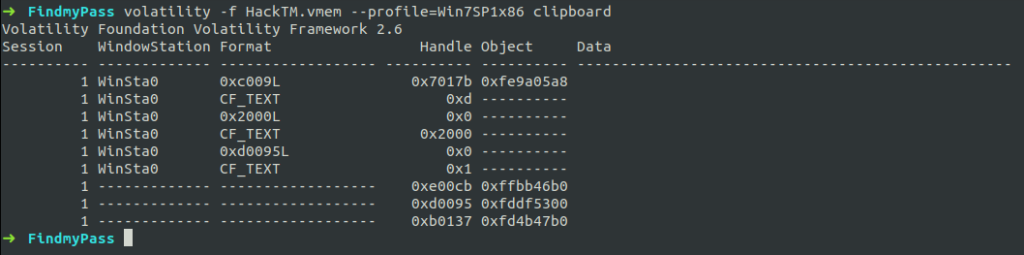
We can’t find anything in the clipboard. It seems to be suspicious. So let’s check the verbose data of the clipboard.
$ volatility -f HackTM.vmem --profile=Win7SP1x86 clipboard -v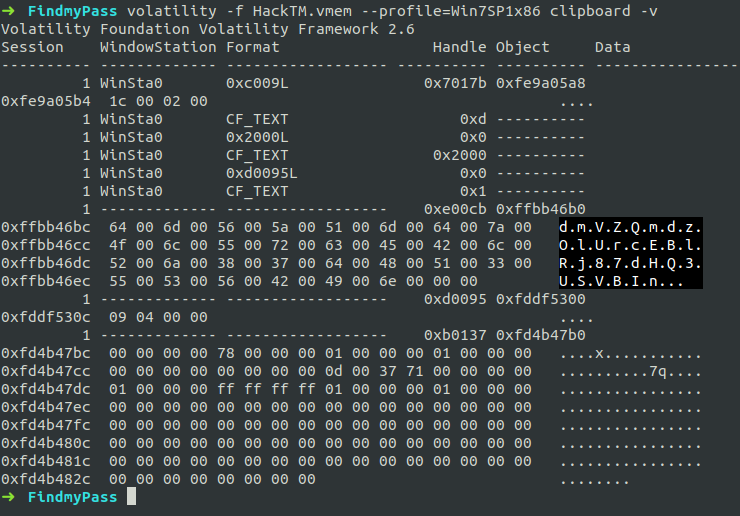
Hurrah! We found it.
By removing the dots and using it (dmVZQmdzOlUrcEBlRj87dHQ3USVBIn) as the master password we got into the Keepass database.
In the bottom, in attachments, we can see that there is nothinghere.7z file that was attached to the password entry.
We can extract that from the File Attachments in the Advanced tab of Edit Entry.
The 7z file asked for a password and on using the database master password we successfully extracted the text file. It contained the flag.
Flag: HackTM{d14c02244b17f4f9dfc0f71ce7ab10e276a5880a05fca64d39a716bab92cda90}
The another way of solving this challenge is mentioned in blog.bi0s.in by my mentor @_abhiramkumar.
If you like my solution, please do share it. I’m availabe on Twitter: @NihithNihi

