I have solved this challenge after the CTF.
Initial Analysis
We are given with a windows 7 memory dump, lets start out initial analysis and check what all processes are running.
$ volatility --plugins=../../Tools/volatility-plugins -f Based.raw --profile=Win7SP1x64 pslist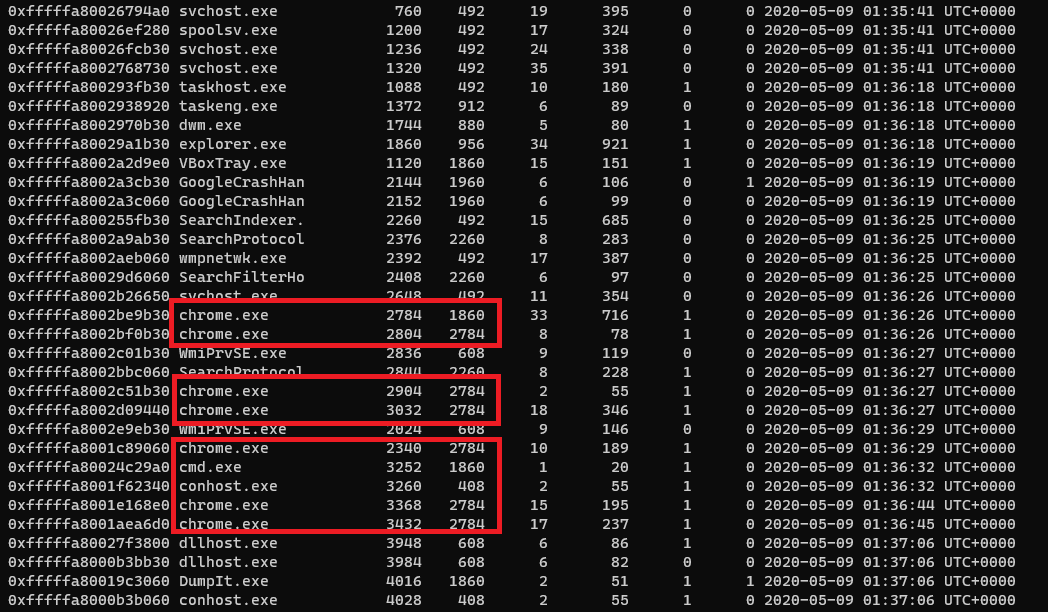
We can see that Google Chrome and Command Prompt are active running process. So let us dig more into them and check whats there in them.
Further Analysis
As we know each and every command we entered in command prompt are stored in conhost.exe and we can retrive those commands from volatility’s consoles plugin.
$ volatility --plugins=../../Tools/volatility-plugins -f Based.raw --profile=Win7SP1x64 consoles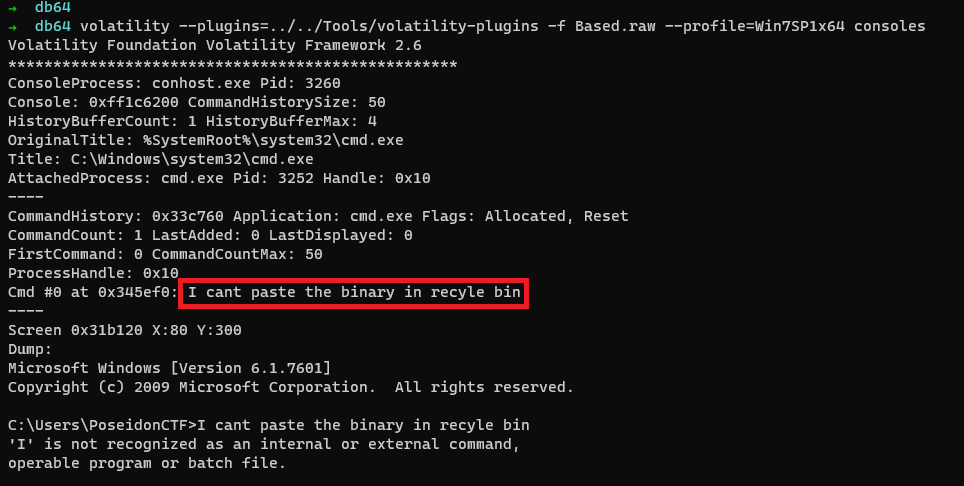
We can see “I cant paste the binary in recyle bin“ which gives us an information that we have to proceed to pastebin for the next step. But we need a random 8 letter character.
On going through some plugins, used mimikatz to get the user password. And found something similar to that random 8 letter character for pastebin.
$ volatility --plugins=../../Tools/volatility-plugins -f Based.raw --profile=Win7SP1x64 mimikatz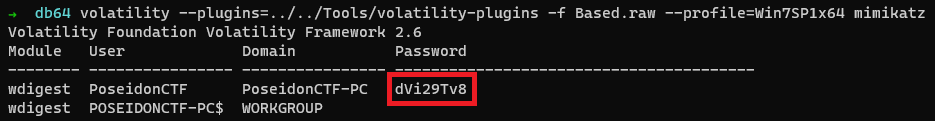
So on proceeding to this pastebin link(https://pastebin.com/dVi29Tv8) and we can see a lot of strings of length 37. So it much be some kind of wordlist or something.
Let us check whats there in chrome history.
$ volatility --plugins=../../Tools/volatility-plugins -f Based.raw --profile=Win7SP1x64 chromehistory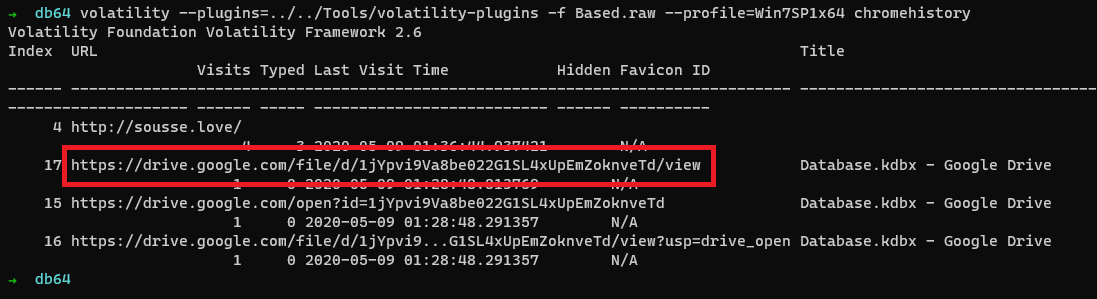
We can see that there is drive link(https://drive.google.com/file/d/1jYpvi9Va8be022G1SL4xUpEmZoknveTd/view) is present and after opening it we found an keepass database.
For opening these keepass database we need a Master Password or Key file. But we can’t find one in the given memory, so as we know we can crack Keepass passwords with John the ripper and get the password if we have the correct wordlist.
Using the strings found in the pastebin as a wordlist we got the password.
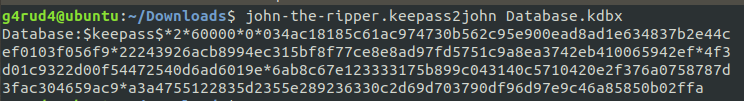
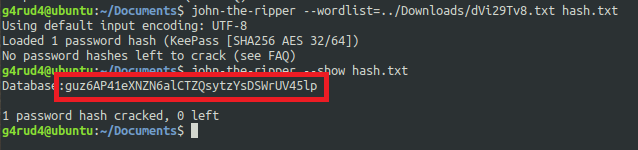
As I have already loaded the hash and its showed its already cracked. And we can see the cracked hashes also and we got the password as this guz6AP41eXNZN6alCTZQsytzYsDSWrUV45lp and after opening the keepass with that password we can see so many passwords already there in the database. From the username we can see that Pastebin/KEY. And the passwords are also something similar to 8 letter random characters needed for pastebin.
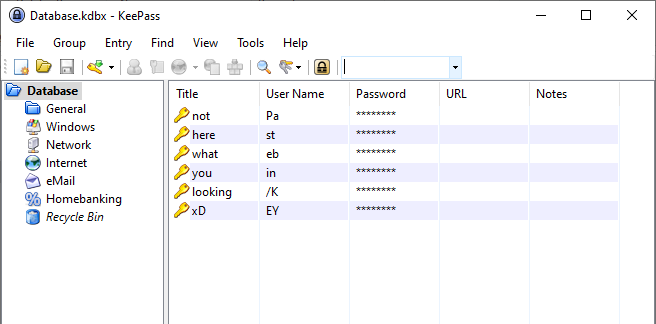
After going through them and we can see a long base64 string in all the pastebins and decoding those base64 strings and there are a lot of fake flag and in that one them is flag.
Flag


