tl;dr
- Decoding the strings found in TCP stream 0.
- Analysing and extracting data sent via different ports of TCP.
- Using character-wise caesar from the extracted data.
- Zip cracking
Challenge Description
You can download the challenge file from Mega or G-Drive
This is a challenge which I made for InCTFi’19 along with my teammate(@Sh4d0w).
Initial Analysis
We are provided with a pcap file. Let’s start our initial analysis.
We can see so many TCP packets in the capture file and the description says that it was a chat between two friends. So let’s follow the TCP stream and see if anything is interesting in it.
We do see a chat between 2 people. Also, we can find some encoded strings. The secret code: Remember remember the FIFTH of november :) does hint out something. We can assume the encoded strings are ROT5. Decoding them, we get;
Rohith: This is a sample in that encoded way.
Shyam: Oh, It's good and it took a lot of time to understand for me.
Rohith: Sending you some interesting files, try to find the secret behind them and keep it confidential
Shyam: Okay, sure:)Further Analysis
As the chat between them says that some files have transferred. And we can see that from TCP Stream 2, extra data with 800 bytes is transferred in two different destination ports(444 & 81). We can assume that the two files have been transferred.
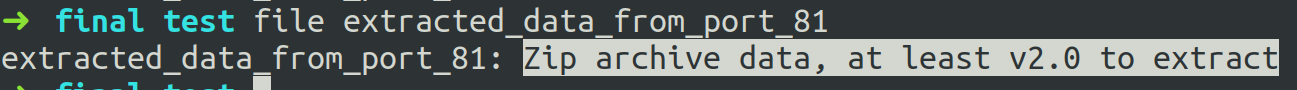
Extracting the data sent to the above-mentioned ports and applying Caesar cipher on the two files, we get the file structure of a PDF file and a ZIP file.
After opening the PDF and we find extra spaces in the last page of that file. It says “NOTHING HERE :( DON’T WASTE YOUR TIME“.
So it’s just a rabbit hole.
After a brief observation, we see that the ZIP is password protected. So, we use fcrackzip in dictionary mode to crack the password,
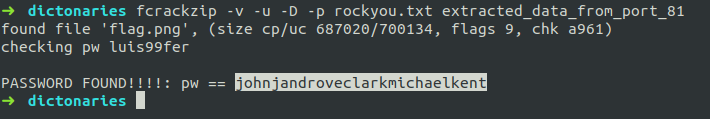
The password is johnjandroveclarkmichaelkent.
Extracting the file from the zip gave a PNG image.

Flag
Simple LSB steg can be used to get the flag. We used the popular tool zsteg for this.
FLAG: inctf{3ach_4nd_3v3ry_s3cre7_inf0rm4t10n_w1ll_b3_kn0wn_by_wir3shark!!!!!_:)}
If you like my solution, please do share it. I’m availabe on Twitter: @NihithNihi

